Everyone agrees that passwords are bad, yet we continue to create systems that use them. For businesses operating applications, whether they be for internal or public use, the risks associated with account compromise are truly terrifying. The financial impact and reputational damage can be devastating to even the largest of businesses. Yet every week, headlines are full of monstrous hacks leading to credential leaks and ransomware exploits affecting some of society’s most popular and often critical systems. It doesn’t have to be this way, it can be addressed but it requires a new approach.
Passwords aren’t the problem, it’s human behavior
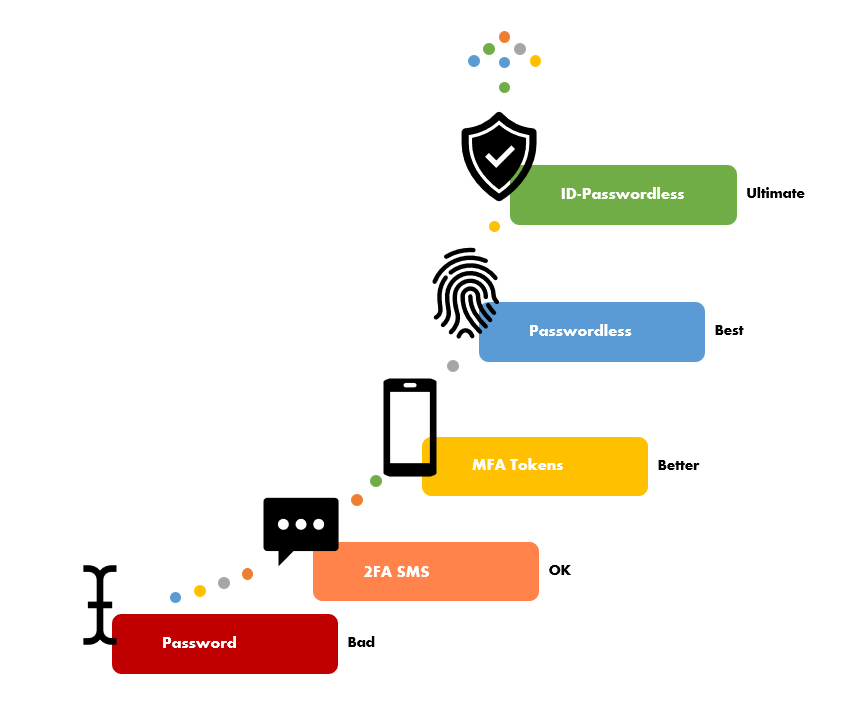
It’s a common misconception that Two Factor (2FA) or Multi-Factor (MFA) Authentication using a one-time-token or an authenticator app is protection enough. Well unfortunately it isn’t.
Another misconception is that humans are the weakest link in authentication. On the contrary, we (our biometrics in particular) ARE the strongest form; but the way in which we handle passwords is weak and provides poor authentication because it doesn’t guarantee the identity of the user. This the issue and its being exploited every second of every day.
This is because MFA still requires users to create a complex ‘p4s5_W0rd@!*’ to secure accounts and these passwords can still be leaked. Today’s technological society forces us all to hold many user ID’s and password combinations. As humans, we re-use our passwords across business and personal accounts because it’s simply too difficult and inconvenient not to. And it doesn’t help when password managers are exploited! So when any compromised account’s password – whether it’s from a 2FA/MFA protected account or not – on leaking, hackers will use that password everywhere until they are successful.
The scary thing is that it’s not usually the initial account access that proves useful to a hacker, more often its used as a stepping-stone to other accounts allowing them to move laterally and pick out high-value targets. All the while going unnoticed by businesses and end-users …. until of course it’s too late.
It won’t happen to us …
It can and unfortunately, it’s far more likely than you may think. Hackers have a wide and ever-growing range of software tools that automate user information scraping across social media accounts which feed sophisticated compromise exploits. They often target the low-hanging fruit of likely business services (such as email, messaging, collaboration, code repositories, CRMs etc.) to get one foot in the door.
The reality is that it only takes one user to unwittingly compromise your business and there’s a good chance you’ll be dealing with a full-blown cyber incident. The very best-case scenario is that you have a highly skilled in-house cyber response team ready to mobilise at a moment’s notice and set about minimizing the impact.
Unfortunately, it’s more likely that effected businesses are placed firmly on the back foot, unable to explain exactly what has happened and forced to take drastic measures which last days if not weeks and months to recover from.
Clearly a serious cyber incident is not a situation any business wants to find themselves in. Poor handling of cyber incident or downplaying its impact could easily see business owners personally liable and land them in the courts on charges of negligence.
So how do we fix this?
First of all, assume that any site or application that uses only username and password with no means of 2FA/MFA is insecure. The best advice is to not operate these systems within your business. If you must, identify them as security risks and make plan to phase them out. Fortunately, applications and authentication systems from the likes of Google, Apple and Microsoft support FIDO2 Passwordless Authentication. Enable them and allow users to use their mobile devices or dongles such as a YubiKey to hold their passwordless keys.
For applications that you have built yourselves, these can benefit from the same level of security by plugging-in a passwordless service.
At Arissian, we’ve created a passwordless authentication service that allows passwords to be removed from user accounts, mitigates authentication-related cyber-attacks and ensures that access to accounts is by a real person and importantly, the one you expect.
Luciditi Sign-In uses biometrics linked a verified identity in the Luciditi App. There are no passwords or OTP codes, instead a users’ biometrics and their Verified ID are the authentication.
By adding a users’ true Identity to the passwordless authentication process, Luciditi Sign-In will elevate your secure authentication even further than regular passwordless authentication. We call this “ID-Passwordless”
What’s involved in moving your own apps to ID-Passwordless Authentication?
We recognise that re-engineering any authentication process is daunting, especially when it involves removing something as fundamental as the password – we know because we’ve done it ourselves. So we’ve simplified things.
All you need is a Luciditi Business Account which comes with credentials and code-snippets you’ll need for integration.
Once your Luciditi account is verified and active, it’s possible to implement our highly secure, ID-backed passwordless technology in just a few hours. You don’t need to spend time researching the underlying open standards technology associated with passwordless (FIDO2, WebAuthn, CTAP2) we’ve wrapped up everything you need into two simple api functions, “Register” and “Sign-in”. It’s a very simple, low code piece of work. Plus, if you need a hand at any point, our team of developer experts are on hand to guide you every step of the way.
To get an idea of how a Luciditi Sign-In process works using a fictious demo web site, take a look at the video below. This example allows a user to scan a QR code or initiate authentication directly using your own use account identifier (in this case we’re using a Luciditi username). If opened from a mobile browser, an app-link attached to a single ‘Login’ button could be used in place of both options
The Desired Outcome
Once you have enabled Luciditi Sign-In in your application:
- Accounts will be protected with a highly secure, ID-backed, FIDO2 compliant authentication.
- Initiate Sign-In through QR Code Scan, Mobile Push or Luciditi Realtime Request
- User Sign-In is two-taps on a mobile device
- You know that the person signing in has done so using their own biometrics on a dedicated device
- Users can self-register devices via a common FIDO2 enrollment experience
- Man-in-the-middle attacks are rendered useless
- Brute-force hacking of passwords no longer a concern
- Cost associated with IT managed password resets goes away
- No costs associated with sending OTP via SMS
- No honey pot of username/passwords in your user data so better data security compliance/lower risk
But perhaps the most important benefit is that you will have played your part in the non-proliferation of passwords – because reducing password use reduces cybercrime.
Want to know more?
If you would like to find out how Luciditi Sign-In can help secure your environments contact us for a chat today.