Identity verification is usually a one-way street. Security-conscious companies demand access to personal documents before they trust you. But how far can you trust them? The new Luciditi digital ID app significantly cuts the risk of your details being breached, as recently experienced by a third of the population of Australia.
When Optus, Australia’s second-largest telecommunications provider, was hacked in September 2022, as many as 10 million accounts were exposed. Names, dates of birth and phone numbers were accessed by a person or people who demanded a ransom of a million dollars.
A database that beckons hackers, like a giant Aladdin’s cave, is always risky. Once breached, everything’s up for grabs. Now, for the first time, businesses have a viable alternative – and so do we, their customers.
Luciditi, an Digital Identity Platform from a British team of data security experts, lets you upload your ID documents to a personal digital wallet on your phone, so that relevant details (known in the trade as ‘information attributes’) can be shared with those who need to know. No need to send anything via email, social media or postal snail mail. Accessed by photo facial matching with liveness detection, everything is sealed behind military-grade encryption.
Reducing the risk of a breach
Data breaches have far-reaching consequences that individuals can do little to prevent. According to the UK government’s survey of cyber security breaches (2022), 39% of UK businesses identified a cyber-attack in the previous year, though the true number is probably higher. In the US, the 2021 Thales Data Threat Report found that 45% of companies had experienced a recent breach.
Internal mistakes are just as dangerous. The personal details of 900,000 Virgin Media customers were leaked in 2020 after a database was left open for 10 months. Individuals expect organisations’ data security to be regulated by government departments and independent authorities. However, the UK’s Financial Conduct Authority itself has admitted leaking personal data, so too the Home Office which has apologised, three times, for unauthorised breaches of data.
Luciditi substantially reduces these risks. It works like this. An organisation invites you to sign up to them, requiring you to prove your identity via the Luciditi app. Individuals download the app for free – running costs are paid by Luciditi’s corporate clients.
The organisation you’ve signed up to gives you a public key to their side of the app, which you then use to create your own personal wallet where you upload your details and ID documents.
Within your wallet, each document or other piece of data is separately encrypted, and your personal key (held on your device) is known only to you. No-one else has the key, including Luciditi.
Users joining Luciditi consent to data being gathered from their credit record, the electoral roll and other government-backed sources that confirm their name, age and address. Supported by a live selfie, this information is combined into a digital ‘Luciditi identity’ that individuals can then use at will, whether they need to sign up to a utility company or prove their age at a venue. Users are effectively signing up to a ‘network of trust’, in which all other participants have been verified.
Proven industry expertise
Developed in-house over nearly four years by tech company Arissian, based in Birmingham, Luciditi benefits from the success of the company founders’ previous ventures in UK healthcare, among them Docman. Bringing iron-clad security to sensitive medical data in volume, Docman holds clinical documents for two-thirds of the UK population.
Phil Young, Chief Technical Officer of Arissian, says: “As the recent catalogue of high-profile data breaches prove, even large organisations aren’t necessarily the best equipped to keep your data safe.
“Many businesses haven’t upgraded their data security and privacy technology at the pace required both by the modern customer in terms of a speedy registration process and, most importantly, to ensure the vast and growing cache of personal information now required to stay on file is kept as secure as possible.”
Young, along with co-founder Ian Moody, initially developed Luciditi as a spin-off from a patient consent system. They saw that their pioneering solution, allowing sensitive information to be securely shared between patients and clinicians, had wider potential in other sectors in which individuals need control of their own data.
Protecting users from the start
Luciditi’s healthcare heritage gives it a valuable sense of trust, all too often missing from other identification systems. Since these primarily support the global corporates that own them, customers can do little more than hope that their own interests are safeguarded.
Once you’ve given your details and documents to one of these firms, you as an individual have little say over how they protect that information or how long they hold it for. You might be careful in protecting your own security, but once your data’s out the door you’re at the mercy of others. Luciditi is alone in thinking of individuals from the start, restoring trust to the relationship by giving them greater control, along with a sense of reassurance and agency.
Seeking to build a re-usable platform Ian Moody says: “We wanted to protect the end-user in the process as much as we would the organisation implementing – surprisingly, this is not a fundamental feature of other systems in the market, it’s typically very one sided and not on that of the individual.”
Luciditi enables users to upload their documents and then make them available to multiple operators. It can recognise genuine documents from thousands of different types used across the world – everything from drivers’ licenses, temporary visas through to passports from 250+ countries.
Using the app to provide immediate consent to share or identity, individuals can devote less time to scrabbling around looking for a utility bill each time they need to sign up to something.
No need for ID to get into a venue
While finance companies need to inspect personal documents, businesses such as social media platform Curv use the app only to confirm identity, without routinely requiring access to personal data. Curv can only reach original documents in rare ‘break-glass’ situations, (such as providing the identity of an individual to authorities) – through a feature known as GlassVault, unique to Luciditi.
Curv, which is seeking to restrict the anonymity that’s harmful to other social media platforms, can assure users that it has the capability to prove identity, without taking the intrusive steps of more regulated sectors.
Luciditi also permits real-time identity and age verification, either in the room or remotely. Operators asking for proof receive a reply confirmed by documents which remain hidden behind encryption. People entering a venue don’t need to reveal or even carry personal identification, the app does the job for them.
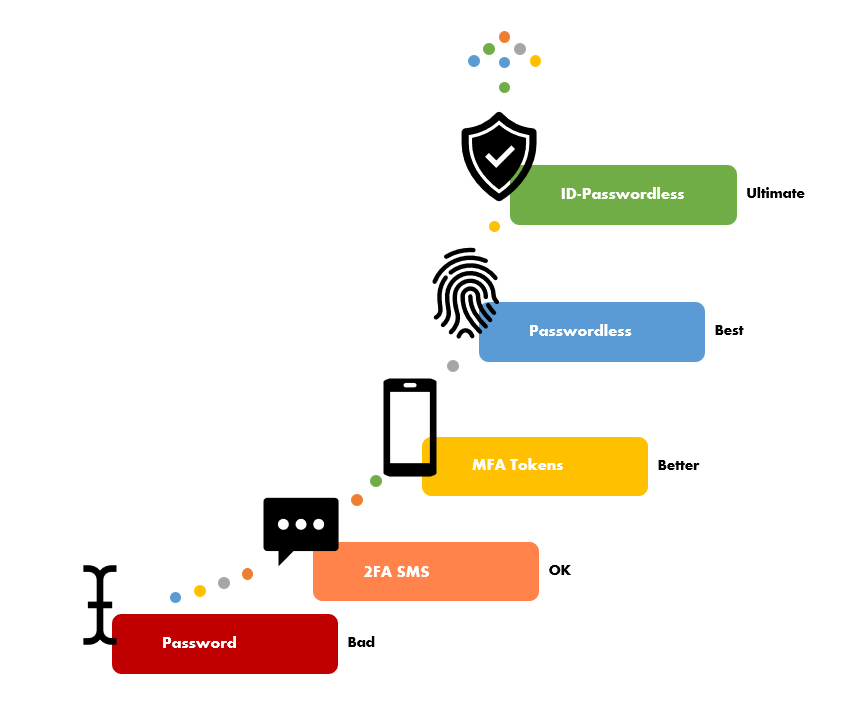
Passwordless sign-in
Luciditi’s smart innovations also let individuals access websites and apps more securely than via a password. A vaguely scrambled combination of the numbers in your birthday is an easy target for hackers. Worse, passwords are frequently recycled – it’s too difficult and inconvenient not to – which makes them particularly vulnerable. Once breached, they become a stepping-stone to swathes of your digital life.
A much stronger form of security relies on biometrics. Luciditi incorporates a package of web authentication standards (FIDO2, WebAuthn, CTAP2), supported by the likes of Google, Apple and Microsoft, enabling seamless access to apps and authentication systems. Your biometrics, combined with your verified Luciditi ID, get you through the door faster than by typing in a one-time password code, or a number generated by an authenticator app.
To activate Luciditi’s passwordless sign-in technology, you simply scan the QR code of the app you want to access, or enter your Luciditi username and then tap the sign-in button. That’s it. Over time you’ll be able to reduce dependency on passwords, your security will increase and with it your peace of mind.
Ultimately, Luciditi’s package of security features seriously raises the bar in the level of protection that individuals can expect from their online relationship with businesses. Data is available only as long as both sides deem necessary, users can see if their data has been seen, and access can be readily revoked. The app’s compartmentalised design, encrypting and protecting individual documents, limits the need for an Aladdin’s cave database, builds trust on both sides and significantly restores the balance of power between concerned individuals and vulnerable corporate giants.
Want to know more?
If you would like to find out how Luciditi can protect your business contact us for a chat today.